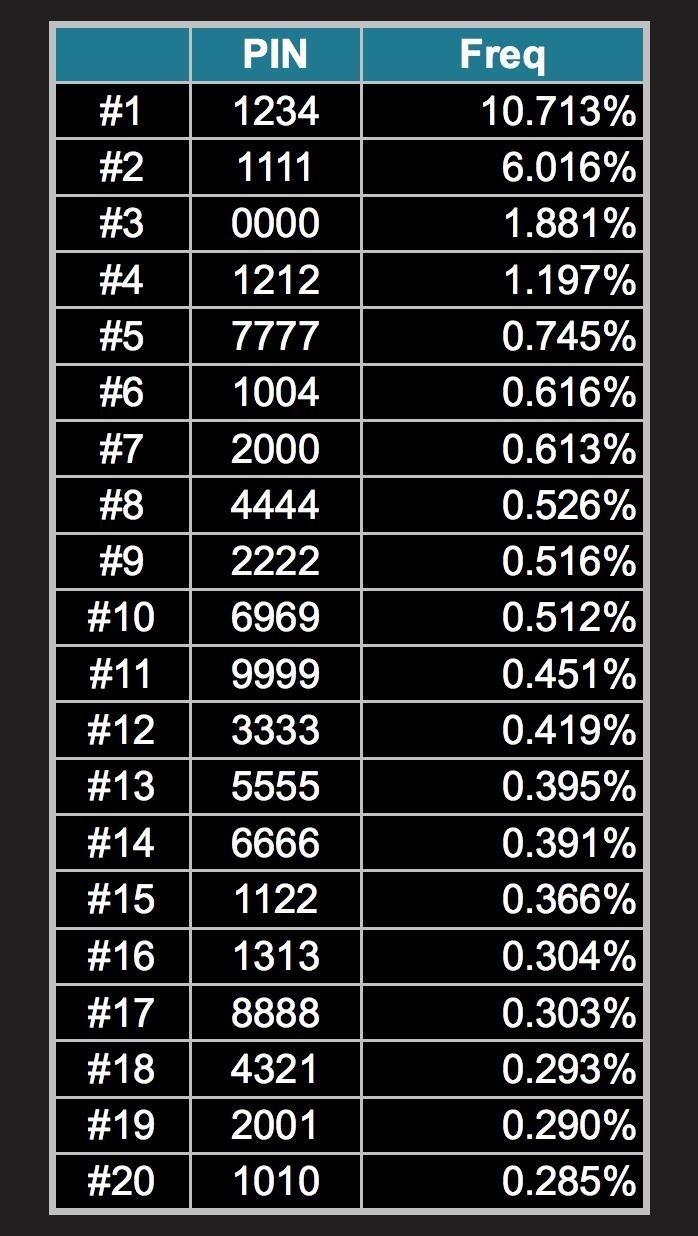
According to a blog post by Nick Berry, a former rocket scientist and current president of Data Genetics, there are 10,000 possible combinations for a 4-digit PIN using the numbers 0-9. And out of that myriad of possibilities, nearly 11% of all PINs being used are "1234". Surprised? No? I'm not surprised.
So, if four-digit personal identification numbers were actually bird species, that means that everybody prefers sparrows, or simply SPAR, as their passcode.
So, what does this teach us? Use better PINs, because it's not only important for keeping thieves from stealing your dough from ATMs, but it's also very important for keeping law enforcement out of your smartphone. How many of you actually use "2580" as your iPhone's passcode? Really? How about your voicemail PIN code? Yeah.
So What Numbers Don't You Use?
- Don't use any patterns.
- Don't use any birth dates.
- Don't use any repeating digits.
- Don't use any years.
- Don't use the same PIN for your smartphone as your debit card.
- Don't use the most commonly unused PIN, "8068", because now everybody knows it.
- Don't use the last 4 digits of your social security number.
- Don't use the last 4 digits of your phone number.
- Don't use your address number.
- Don't use the PIN that came with your credit or debit card.
- Don't use the last four digits of you credit or debit card number.
What PINs Do You Use Then?
- Do use four different digits that don't apply to any of the above.
- Do change your PIN every month to keep hackers on their toes.